Securely Handling Sensitive Output in Terraform
Learn secure techniques for handling and displaying sensitive data output variables in your Terraform projects without compromising security.
Learn secure techniques for handling and displaying sensitive data output variables in your Terraform projects without compromising security.
Terraform provides a mechanism to protect sensitive information like passwords and API keys by allowing you to mark output variables as sensitive. While this hides the values from standard console and log output, there are situations during testing or debugging where you might need to access these values. This article will guide you on how to safely retrieve sensitive output values in Terraform using the command line and JSON parsing.
Terraform allows you to mark output variables as sensitive to protect confidential information. When you mark an output as sensitive, its value will be hidden from the console and log output. However, there are situations where you need to access these sensitive values, such as during testing or debugging.
To view the sensitive output values, you can use the terraform output command with the -json flag. This will output all output values, including sensitive ones, in JSON format. You can then parse this JSON output to extract the specific sensitive value you need.
Here's an example:
Let's say you have an output variable named db_password that is marked as sensitive:
output "db_password" {
value = random_password.password.result
sensitive = true
}To retrieve the value of db_password, you can run the following command:
terraform output -json
This will output all output values in JSON format. You can then use a tool like jq to extract the value of db_password:
terraform output -json | jq -r '.db_password.value'
This will print the value of the db_password output variable to the console.
Note: It's important to handle sensitive values with care and avoid exposing them in insecure environments.
This Terraform code defines a resource for generating a random password and two output variables: one sensitive (db_password) for the password and one non-sensitive (db_username). It explains how to retrieve the sensitive output value using 'terraform output' command with '-json' flag and then extracting the value using 'jq'. The description emphasizes handling sensitive information with caution and suggests exploring secure alternatives like HashiCorp Vault.
This example demonstrates how to define a sensitive output variable in Terraform and retrieve its value using the terraform output command and jq.
main.tf:
resource "random_password" "password" {
length = 16
special = true
}
output "db_password" {
value = random_password.password.result
sensitive = true
}
output "db_username" {
value = "admin"
}This code defines:
db_password that stores the generated password. The sensitive = true argument marks this output as sensitive, hiding its value in the console.Retrieving the sensitive output:
Run terraform apply: This will create the resource and display the output variables, hiding the value of db_password.
Retrieve all outputs in JSON format:
terraform output -jsonThis will output something like:
{
"db_password": {
"sensitive": true,
"value": "your_hidden_password"
},
"db_username": {
"sensitive": false,
"value": "admin"
}
}Extract the value of db_password using jq:
terraform output -json | jq -r '.db_password.value'This will print:
your_hidden_password
Important considerations:
This example demonstrates how to retrieve sensitive output values in Terraform. Remember to handle this information responsibly and prioritize security best practices.
jq: While jq is a powerful tool for JSON parsing, you can also use other tools or scripting languages like Python to extract values from the JSON output.terraform console: For interactive usage, terraform console allows you to access output values, including sensitive ones, directly within a console session. However, exercise caution as the console history might retain sensitive data.While Terraform protects confidential information by hiding sensitive output variables from console and log output, you can still access these values for testing or debugging purposes.
How to access sensitive output values:
terraform output -json command: This outputs all output values, including sensitive ones, in JSON format.jq to extract the specific sensitive value you need.Example:
To retrieve the value of a sensitive output variable named db_password, you would run:
terraform output -json | jq -r '.db_password.value'
Important Note: Always handle sensitive values with care and avoid exposing them in insecure environments.
In conclusion, Terraform's ability to mark output variables as sensitive provides a valuable layer of protection for confidential information. While these values are hidden by default in console and log outputs, you can still access them when needed for tasks like testing or debugging. By using the terraform output -json command and a JSON parsing tool like jq, you can retrieve specific sensitive values. However, it's crucial to exercise caution and adhere to security best practices when handling such information. Remember to protect your state files, consider secure storage solutions like HashiCorp Vault for sensitive values, and always prioritize the principle of least privilege. By understanding these techniques and best practices, you can leverage Terraform's capabilities while maintaining the security of your infrastructure and sensitive data.
 How to show sensitive values - Terraform - HashiCorp Discuss | I can see how sensitive values need to be protected in CI/CD, but at my terminal I would like to see them. In some cases, there is a workaround, eg for outputs that are marked sensitive you can use json output. BUT this trick does not work for terraform apply: sensitive values are masked, and if the value is say a json blob (created from a template), the whole blob is masked. There is then no way for me to know what actually caused the change in that json/value. Is there a way to tell terraform...
How to show sensitive values - Terraform - HashiCorp Discuss | I can see how sensitive values need to be protected in CI/CD, but at my terminal I would like to see them. In some cases, there is a workaround, eg for outputs that are marked sensitive you can use json output. BUT this trick does not work for terraform apply: sensitive values are masked, and if the value is say a json blob (created from a template), the whole blob is masked. There is then no way for me to know what actually caused the change in that json/value. Is there a way to tell terraform... Protect sensitive input variables | Terraform | HashiCorp Developer | When you do so, you need to ensure that you do not accidentally expose this data in CLI output, log output, or source control. Terraform provides several ...
Protect sensitive input variables | Terraform | HashiCorp Developer | When you do so, you need to ensure that you do not accidentally expose this data in CLI output, log output, or source control. Terraform provides several ... Output Values - Configuration Language | Terraform | HashiCorp ... | ... data will have access to the sensitive values in cleartext. For more information, see Sensitive Data in State. depends_on — Explicit Output Dependencies.
Output Values - Configuration Language | Terraform | HashiCorp ... | ... data will have access to the sensitive values in cleartext. For more information, see Sensitive Data in State. depends_on — Explicit Output Dependencies.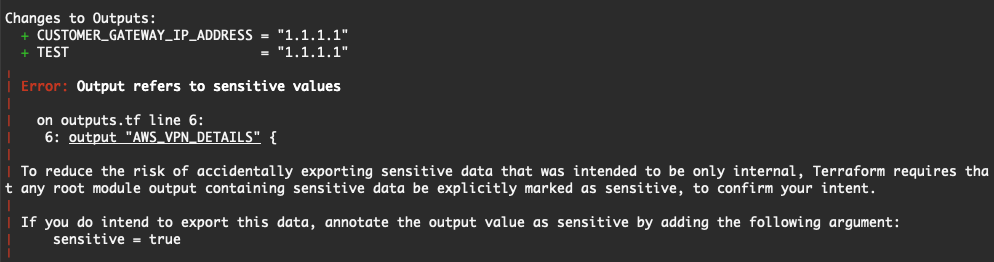 Decoding Sensitive Outputs in Terraform | by Shiva V | AWS Tip | It happened so while I was building an awesome multi-cloud hands-on lab using Terraform, that I ran into a peculiar error.
Decoding Sensitive Outputs in Terraform | by Shiva V | AWS Tip | It happened so while I was building an awesome multi-cloud hands-on lab using Terraform, that I ran into a peculiar error. Terraform - Sensitive Output - DEV Community | DevOps - Terraform - Sensitive Output
Terraform - Sensitive Output - DEV Community | DevOps - Terraform - Sensitive Output