Terraform Multi-Account Deployment: A Complete Guide
Learn how to efficiently and securely deploy your infrastructure to multiple AWS accounts using Terraform, simplifying your workflow and enhancing governance.
Learn how to efficiently and securely deploy your infrastructure to multiple AWS accounts using Terraform, simplifying your workflow and enhancing governance.
Managing infrastructure across multiple AWS accounts is a common requirement for organizations seeking to enhance security, separation of concerns, or compliance. Terraform, a popular Infrastructure as Code (IaC) tool, provides robust capabilities to streamline this process. This article outlines essential practices for effectively managing multiple AWS accounts using Terraform, enabling you to orchestrate resources seamlessly across your environments.
Utilize multiple provider configurations: Define separate provider blocks within your Terraform configuration file for each AWS account you want to target. Each provider block should have a unique alias assigned to it.
provider "aws" {
region = "us-west-2"
alias = "dev"
}
provider "aws" {
region = "us-east-1"
alias = "prod"
}Leverage provider aliases: When defining resources that should be deployed to a specific AWS account, reference the corresponding provider alias using the provider argument within the resource block.
resource "aws_instance" "dev_instance" {
ami = "ami-0c94855ba95c574c8"
instance_type = "t2.micro"
provider = aws.dev
}
resource "aws_instance" "prod_instance" {
ami = "ami-0c94855ba95c574c8"
instance_type = "t2.micro"
provider = aws.prod
}Implement authentication for each account: Ensure that you have configured appropriate AWS credentials for each provider alias. This can be achieved through environment variables, AWS profiles, or other supported authentication methods.
Organize your code: Structure your Terraform code in a modular and reusable manner. Consider using modules to encapsulate resources specific to each AWS account or environment.
Employ remote state management: Utilize a shared state backend, such as AWS S3, to store the Terraform state file. This enables collaboration and ensures consistency across multiple deployments.
Consider cross-account roles: For scenarios where resources in one account need to interact with resources in another account, leverage AWS IAM roles and assume cross-account access.
Implement security best practices: Follow security best practices, such as principle of least privilege, when configuring IAM roles and policies for cross-account access.
Test thoroughly: Before deploying to production, thoroughly test your Terraform configuration in a staging or development environment to validate its behavior across multiple AWS accounts.
This Terraform code configures two AWS providers, one for a development account and one for a production account. It uses an S3 bucket for remote state management. An EC2 instance module is defined for reusability. The code deploys resources to both accounts, showcasing how to reference specific providers. It includes a commented-out section demonstrating the potential use of cross-account roles. Finally, it outputs the public IP addresses of the deployed instances. Before running, replace placeholders with your specific values, configure AWS credentials, and create the EC2 instance module as instructed in the comments.
# Configure Terraform to use multiple AWS providers
terraform {
required_providers {
aws = {
source = "hashicorp/aws"
version = "~> 4.0"
}
}
backend "s3" { # Use S3 for remote state management
bucket = "your-terraform-state-bucket"
key = "your-project/terraform.tfstate"
region = "us-west-2"
}
}
# Configure AWS Provider for Development Account
provider "aws" {
region = "us-west-2"
alias = "dev"
}
# Configure AWS Provider for Production Account
provider "aws" {
region = "us-east-1"
alias = "prod"
}
# Define a module for deploying an EC2 instance
module "ec2_instance" {
source = "./modules/ec2"
providers = {
aws = aws
}
instance_name = "${var.environment}-instance"
ami = var.ami_id
instance_type = var.instance_type
}
# Deploy resources to the Development Account
resource "aws_instance" "dev_instance" {
provider = aws.dev
ami = "ami-0c94855ba95c574c8"
instance_type = "t2.micro"
}
# Deploy resources to the Production Account
module "prod_instance" {
source = module.ec2_instance
providers = {
aws = aws.prod
}
environment = "production"
ami_id = "ami-0a9d27a4ff2f09d91"
instance_type = "t2.medium"
}
# Example of using cross-account roles (not implemented in this example)
# resource "aws_iam_role" "cross_account_role" {
# # ... Role configuration ...
# }
# Output values
output "dev_instance_public_ip" {
value = aws_instance.dev_instance.public_ip
}
output "prod_instance_public_ip" {
value = module.prod_instance.public_ip
}Explanation:
dev for the development account and prod for the production account.ec2_instance module encapsulates the logic for deploying an EC2 instance, promoting code reusability.aws.dev, aws.prod).output blocks provide information about the deployed resources, such as the public IP addresses of the instances.Before running this code:
dev and prod aliases. This can be done using environment variables, AWS profiles, or other supported methods.modules and a subdirectory named ec2 within it. Then, create a file named main.tf inside the modules/ec2 directory and paste the following code into it:resource "aws_instance" "main" {
ami = var.ami_id
instance_type = var.instance_type
tags = {
Name = var.instance_name
}
}
output "public_ip" {
value = aws_instance.main.public_ip
}This code defines the ec2_instance module, which creates an EC2 instance with the specified AMI, instance type, and name tag.
This comprehensive example demonstrates how to manage multiple AWS accounts using Terraform, incorporating best practices for organization, reusability, and security. Remember to adapt the code to your specific requirements and thoroughly test it before deploying to production.
Configuration and Organization:
Security and Best Practices:
Advanced Techniques:
Troubleshooting and Debugging:
terraform console to experiment with provider configurations, data sources, and expressions to validate your code before deployment.terraform graph command to visualize the dependencies between resources across different accounts, aiding in understanding and troubleshooting deployment issues.This article outlines best practices for managing resources across multiple AWS accounts using Terraform.
Key Concepts:
aws.dev, aws.prod).provider argument within resource blocks to specify the target AWS account using its alias.By following these practices, you can effectively manage infrastructure across multiple AWS accounts with Terraform, ensuring clarity, maintainability, and security.
By implementing these strategies and adapting the provided code snippets to your specific needs, you can leverage Terraform's power to manage infrastructure across multiple AWS accounts effectively. This approach not only streamlines your workflow but also enhances security, promotes code reusability, and ensures consistency across your diverse AWS environments. As you delve deeper into managing multi-account deployments, consider exploring advanced techniques like Terraform remote state data sources and custom modules for cross-account interactions to further optimize your infrastructure management practices. Remember to prioritize security by adhering to best practices such as the principle of least privilege and utilizing secrets management tools. Through a combination of best practices, appropriate tooling, and a well-structured approach, you can confidently manage even the most complex multi-account AWS environments with Terraform.
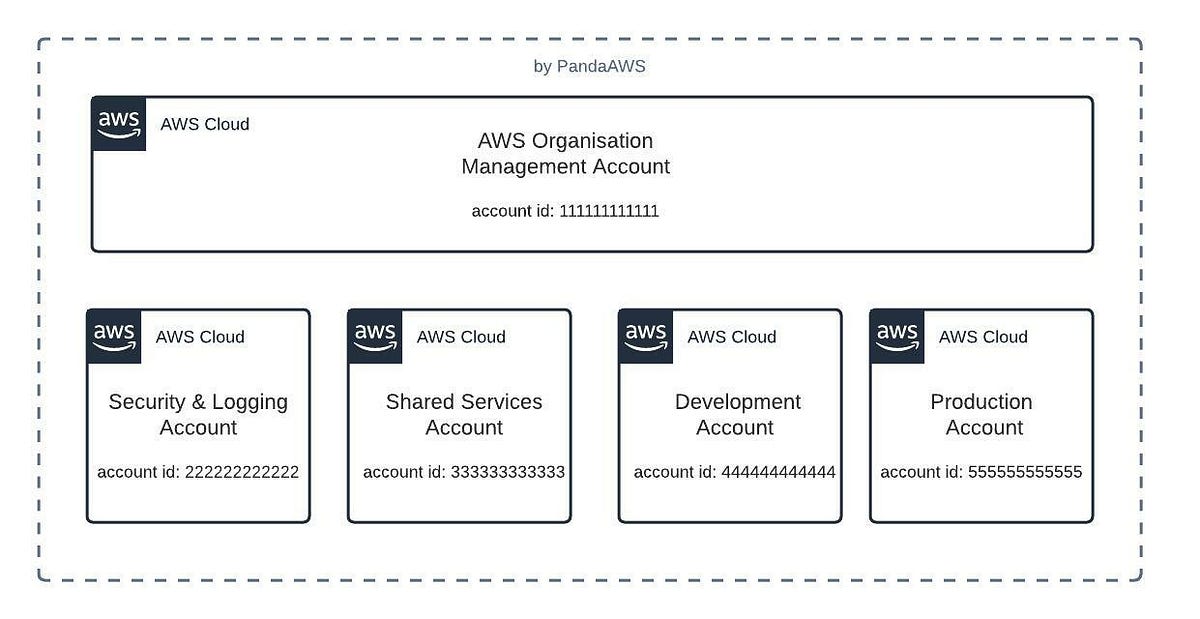 4 steps to deploy to multiple AWS accounts with Terraform | by AW ... | No matter the size of your business, multiple accounts to segregate key functional areas of the AWS environment is always highly…
4 steps to deploy to multiple AWS accounts with Terraform | by AW ... | No matter the size of your business, multiple accounts to segregate key functional areas of the AWS environment is always highly… Terraform multi AWS account deployment - Terraform - HashiCorp ... | Hi everyone, I have 3 different AWS accounts; dev, qa and prod. I have main.tf to create aws vpc. Here is the code of main.tf module "vpc" { source = "terraform-aws-modules/vpc/aws" name = "${var.environment}-vpc" cidr_block = "10.0.0.0/16" tags = { Terraform = "true" Environment = var.environment } } I have backend.tf terraform { backend "s3" { bucket = "${var.environment}/terraform.tfstate-test" key = "terraforn.tfstate" } } I have provider.tf with pro...
Terraform multi AWS account deployment - Terraform - HashiCorp ... | Hi everyone, I have 3 different AWS accounts; dev, qa and prod. I have main.tf to create aws vpc. Here is the code of main.tf module "vpc" { source = "terraform-aws-modules/vpc/aws" name = "${var.environment}-vpc" cidr_block = "10.0.0.0/16" tags = { Terraform = "true" Environment = var.environment } } I have backend.tf terraform { backend "s3" { bucket = "${var.environment}/terraform.tfstate-test" key = "terraforn.tfstate" } } I have provider.tf with pro...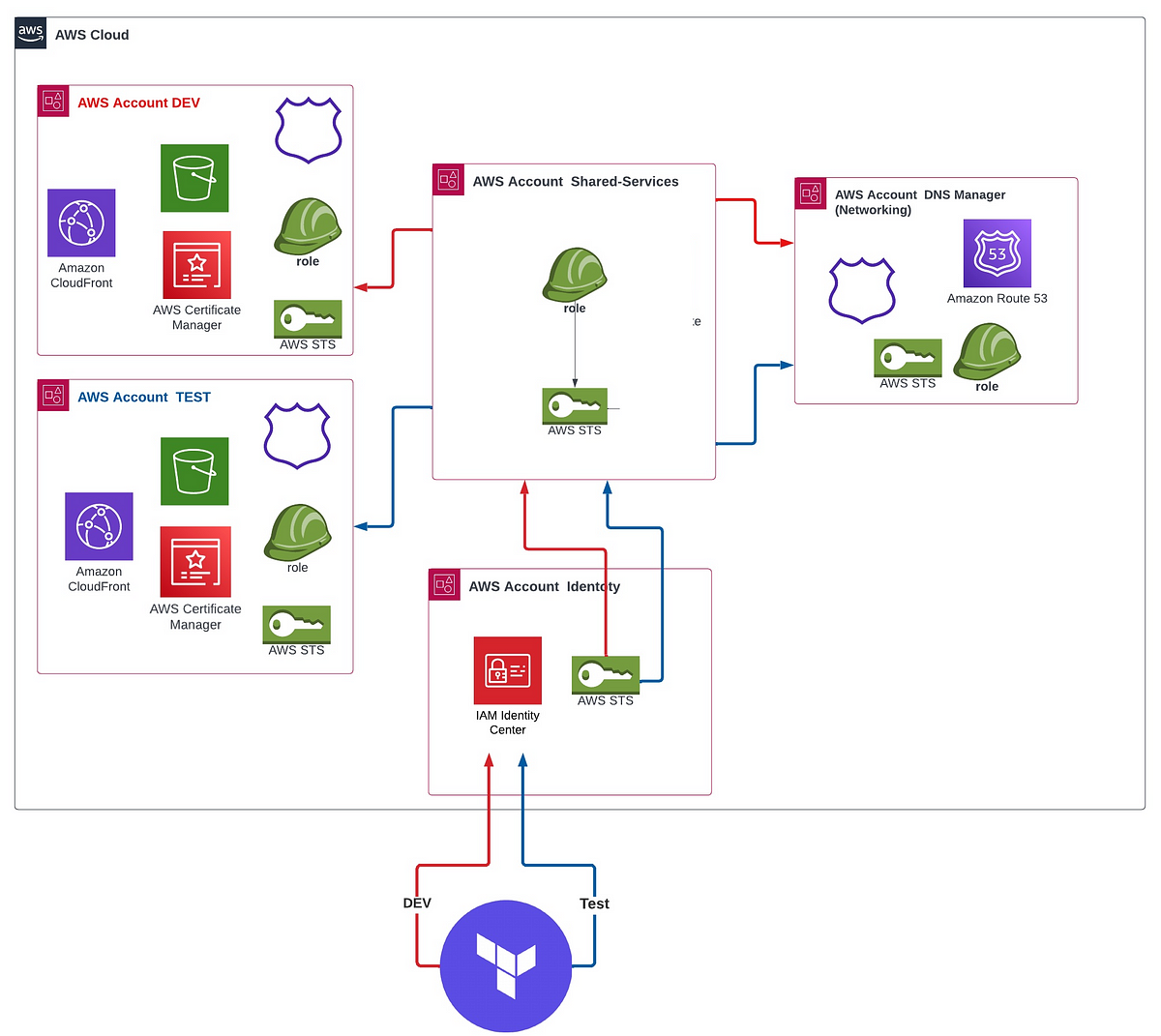 Terraform AWS Provider — Everything you need to know about Multi ... | There are multiple options available to configure the authentication between Terraform and AWS. But the two entry points are IAM users and…
Terraform AWS Provider — Everything you need to know about Multi ... | There are multiple options available to configure the authentication between Terraform and AWS. But the two entry points are IAM users and… Terraform: Deploy To Multiple AWS Accounts In Single Project ... | Generally, when using HashiCorp Terraform to deploy and manage Amazon AWS resources, the Terraform project will be working with AWS resources in only a single
Terraform: Deploy To Multiple AWS Accounts In Single Project ... | Generally, when using HashiCorp Terraform to deploy and manage Amazon AWS resources, the Terraform project will be working with AWS resources in only a single Manage multiaccount and multi-Region infrastructure in Terraform ... | Learn how to reduce the use of managing secret and access keys and quickly deploy all the resources. Use version control to track all changes and enable better control in a multiaccount infrastructure.
Manage multiaccount and multi-Region infrastructure in Terraform ... | Learn how to reduce the use of managing secret and access keys and quickly deploy all the resources. Use version control to track all changes and enable better control in a multiaccount infrastructure. Deploy AWS Resources in Different AWS Account and Multi-Region ... | Introduction As a company with a multi-account AWS setup, we recently faced the challenge...
Deploy AWS Resources in Different AWS Account and Multi-Region ... | Introduction As a company with a multi-account AWS setup, we recently faced the challenge...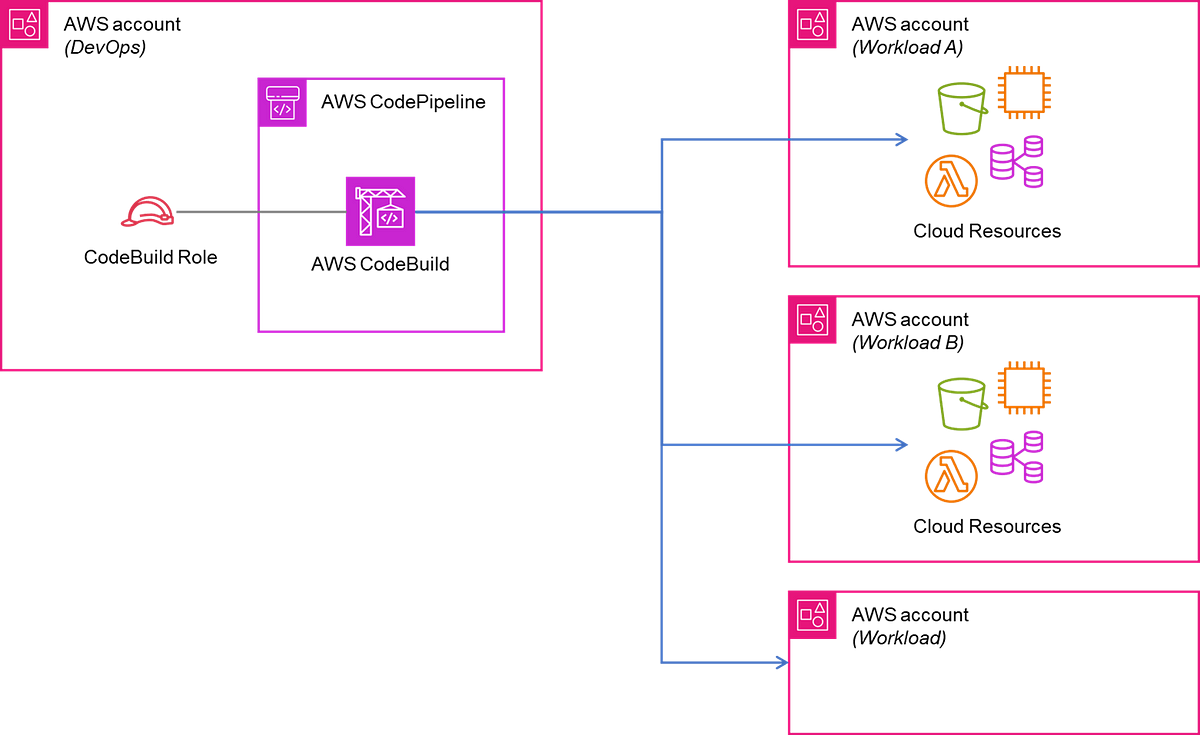 AWS Cross-Account Deployment with Terraform | by KangZheng Li ... | In this article, we will explore using Terraform to do cross-account deployment in AWS.
AWS Cross-Account Deployment with Terraform | by KangZheng Li ... | In this article, we will explore using Terraform to do cross-account deployment in AWS.