AccessControlListNotSupported Error in AWS Bucket ACL
Learn how to troubleshoot and solve the "AccessControlListNotSupported" error encountered when creating a bucket ACL in AWS.
Learn how to troubleshoot and solve the "AccessControlListNotSupported" error encountered when creating a bucket ACL in AWS.
You're encountering the "AccessControlListNotSupported: The bucket does not allow ACLs" error message because you're attempting to use Access Control Lists (ACLs) with an Amazon S3 bucket that has been configured to disable them. This is due to Amazon S3's shift towards a more secure object ownership model that prioritizes resource-based policies, rendering ACLs obsolete. To address this, begin by identifying where you're defining ACLs, whether it's in your code, configuration files, or AWS Management Console settings. Look for parameters like 'acl', 'grant_full_control', or 'grant_read'. If you don't require specific ACL configurations, simply remove these parameters. However, if you need to manage access, transition from ACLs to S3 bucket policies, IAM policies, or object ownership settings. Bucket policies provide a more versatile and secure method for controlling access at both the bucket and object levels. Ensure your bucket's object ownership is set correctly, as ACLs are deactivated if it's set to "Bucket Owner Enforced." Lastly, update any tools or scripts that depend on ACLs to utilize S3 bucket policies or other supported access control mechanisms.
The error message "AccessControlListNotSupported: The bucket does not allow ACLs" occurs when you try to create or modify an Amazon S3 bucket using Access Control Lists (ACLs) but the bucket is configured to disallow them. This is because Amazon S3 now defaults to a more secure object ownership model that relies on resource-based policies and access control lists (ACLs) are no longer used.
Here's how to fix this error:
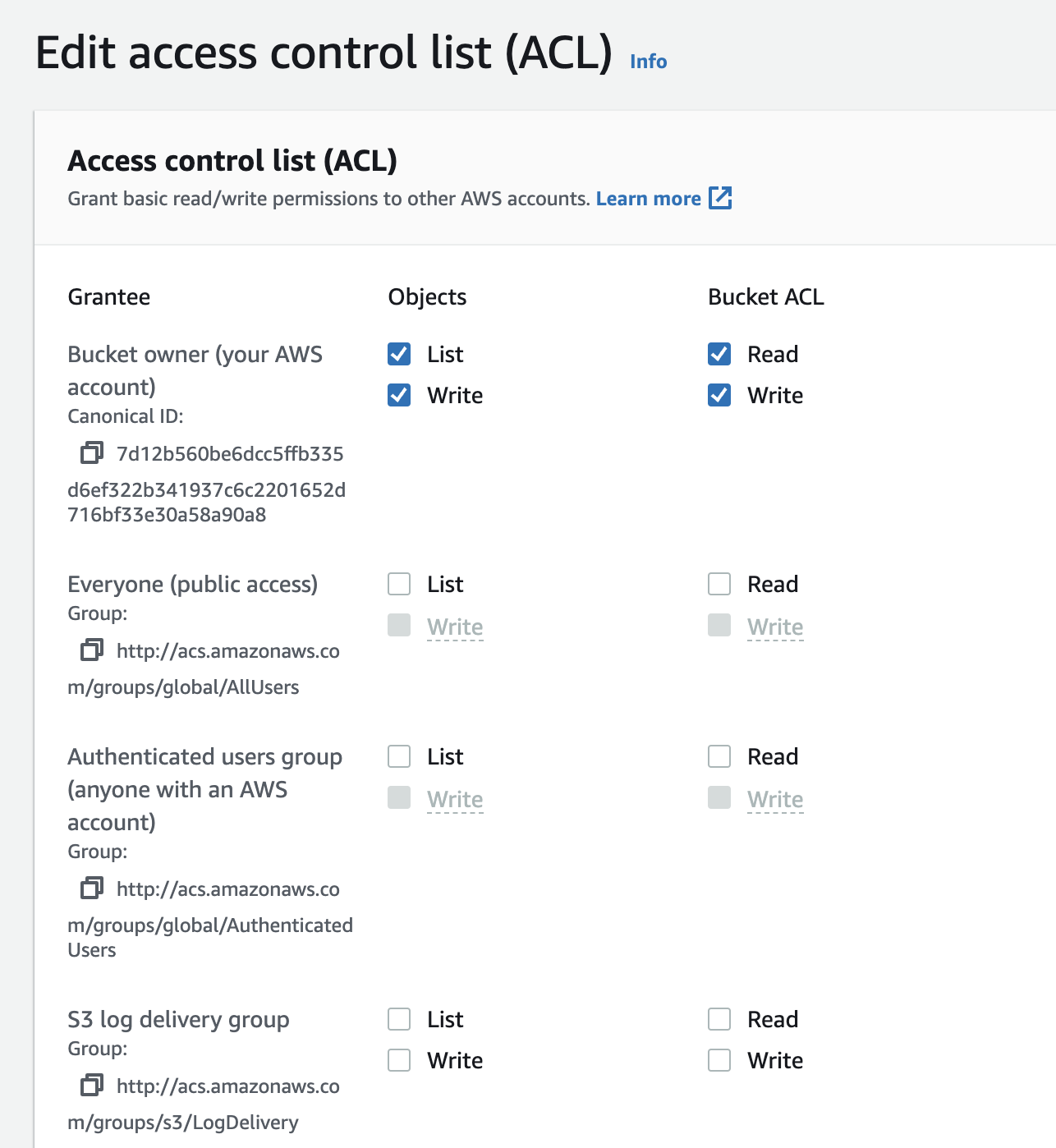
Identify where you're setting ACLs: Check your code, configuration files (like Terraform scripts), or AWS Management Console settings where you're defining the S3 bucket. Look for any parameters related to "ACL," such as acl, grant_full_control, grant_read, grant_read_acp, grant_write_acp, etc.
Remove or adjust ACL settings:
Use S3 bucket policies for granular control: Bucket policies offer a more flexible and secure way to manage permissions at the bucket and object level. You can define who can access what, with conditions like time of day or IP address.
Verify object ownership settings: Ensure your bucket's object ownership is set appropriately. If it's set to "Bucket Owner Enforced," ACLs are disabled, and you'll need to manage access through policies.
Update your tools and scripts: If you're using tools or scripts that rely on ACLs, update them to use S3 bucket policies or other supported access control mechanisms.
By following these steps, you can resolve the "AccessControlListNotSupported" error and ensure your S3 buckets are configured securely using the recommended access control methods.
The Python code uses Boto3 to create an S3 bucket and configures its access using a bucket policy instead of ACLs. It creates a bucket, defines a policy granting public read access to objects within the bucket, and then applies this policy to the bucket. The code emphasizes replacing placeholders with desired bucket names and customizing the policy for specific access permissions.
This example demonstrates how to create an S3 bucket using Boto3 and configure access using a bucket policy instead of ACLs.
import boto3
s3 = boto3.client('s3')
# Create the bucket without ACL configuration
bucket_name = 'my-secure-bucket'
s3.create_bucket(Bucket=bucket_name)
# Define a bucket policy to grant public read access to objects
bucket_policy = {
'Version': '2012-10-17',
'Statement': [
{
'Sid': 'PublicReadGetObject',
'Effect': 'Allow',
'Principal': '*',
'Action': 's3:GetObject',
'Resource': f'arn:aws:s3:::{bucket_name}/*'
}
]
}
# Apply the bucket policy
s3.put_bucket_policy(Bucket=bucket_name, Policy=json.dumps(bucket_policy))
print(f"Bucket '{bucket_name}' created with public read access.")Explanation:
create_bucket() function is used to create the S3 bucket. Notice that no ACL-related parameters are used.s3:GetObject) to all objects (*) within the bucket.put_bucket_policy() function applies the defined policy to the bucket.Important Notes:
my-secure-bucket with your desired bucket name.bucket_policy to define the specific access permissions you need for your use case.This example demonstrates how to transition from ACL-based access control to bucket policies for managing permissions in Amazon S3. By adopting these practices, you can enhance the security and control over your S3 resources.
ACL Deprecation: It's crucial to understand that while you can still technically read ACLs on existing buckets, attempting to set or update them will result in the "AccessControlListNotSupported" error. This emphasizes Amazon's commitment to moving away from ACLs in favor of more modern security practices.
Troubleshooting Existing Scripts: When you encounter this error, prioritize inspecting any infrastructure-as-code scripts (like Terraform or CloudFormation) or automation tools that interact with your S3 buckets. These are common places where outdated ACL configurations might be present.
Object Ownership Implications: The "Bucket Owner Enforced" setting for object ownership is key to enabling more granular access control. When enforced, it automatically disables ACLs, making bucket policies and IAM policies the primary tools for managing permissions.
Public Access Considerations: While the provided Python example demonstrates granting public read access, exercise extreme caution with such configurations. Publicly exposing S3 buckets can lead to security vulnerabilities if not carefully managed.
Alternative Access Control Mechanisms: Beyond bucket policies, explore other access control features provided by AWS:
AWS Documentation: For the most up-to-date information and best practices, always refer to the official AWS documentation on S3 access control: https://docs.aws.amazon.com/AmazonS3/latest/userguide/access-control-overview.html
Security Best Practices: Treat security as paramount. Regularly review and update your S3 bucket policies and IAM policies to ensure they adhere to the principle of least privilege, granting only the necessary permissions.
| Problem | Cause | Solution |
|---|---|---|
| Error Message: "AccessControlListNotSupported: The bucket does not allow ACLs" when creating or modifying an S3 bucket. | Amazon S3 now prioritizes a more secure object ownership model using resource-based policies. ACLs are disabled by default. |
1. Identify & Remove/Adjust ACL Settings: - Check code, configuration files, and AWS Console for ACL parameters (e.g., acl, grant_full_control).- Remove unnecessary ACL settings or replace them with alternative access control methods. |
|
2. Use Alternative Access Control: - Implement S3 bucket policies for granular control over bucket and object access. - Utilize IAM policies to manage permissions for users and groups. - Configure object ownership settings to define access based on object ownership. |
||
|
3. Update Tools & Scripts: - Modify any tools or scripts relying on ACLs to utilize S3 bucket policies or other supported access control mechanisms. |
Key Takeaway: Transition from ACLs to S3 bucket policies, IAM policies, and object ownership settings for a more secure and flexible approach to managing access in Amazon S3.
In conclusion, the "AccessControlListNotSupported" error message, often encountered when working with Amazon S3 buckets, highlights a significant shift in AWS's approach to security. The move away from Access Control Lists (ACLs) towards a more robust, resource-based policy model underscores the importance of adapting to these evolving security practices. By understanding the limitations of ACLs and embracing alternative access control mechanisms like S3 bucket policies, IAM policies, and object ownership settings, developers and administrators can ensure their S3 resources remain both secure and highly accessible. Regularly reviewing and updating these policies, along with staying informed about AWS's latest security recommendations, will be crucial for maintaining a secure and well-managed cloud environment.
 How to fix AWS S3 Error: "The bucket does not allow ACLs" | This blog post offers a step-by-step solution to resolving the AWS S3 error message "The bucket does not allow ACLs" by addressing the underlying cause and providing instructions on how to fix it.
How to fix AWS S3 Error: "The bucket does not allow ACLs" | This blog post offers a step-by-step solution to resolving the AWS S3 error message "The bucket does not allow ACLs" by addressing the underlying cause and providing instructions on how to fix it. How to Fix the Error AccessControlListNotSupported while ... | As a data scientist or software engineer, deploying an Amazon S3 bucket from GitHub is a common task that you might encounter. However, one of the most common errors that you might encounter during this process is the AccessControlListNotSupported error. This error indicates that the bucket does not allow Access Control Lists ACLs which are used to manage access to your S3 bucket. In this article, we will discuss how to fix this error and successfully deploy your S3 bucket from GitHub.
How to Fix the Error AccessControlListNotSupported while ... | As a data scientist or software engineer, deploying an Amazon S3 bucket from GitHub is a common task that you might encounter. However, one of the most common errors that you might encounter during this process is the AccessControlListNotSupported error. This error indicates that the bucket does not allow Access Control Lists ACLs which are used to manage access to your S3 bucket. In this article, we will discuss how to fix this error and successfully deploy your S3 bucket from GitHub. The bucket does not allow ACLs | AWS re:Post | I take my first steps with AWS. I follow this Tutorial step by step:
The bucket does not allow ACLs | AWS re:Post | I take my first steps with AWS. I follow this Tutorial step by step:Deploying a high-availability PHP application with an external Amazon RDS database to Elastic Beanstalk [https://docs.aws.ama...
 Access control list (ACL) overview - Amazon Simple Storage Service | ... (ACLs) or update ACLs fail and return the AccessControlListNotSupported error code. Requests to read ACLs are still supported. When you create a bucket or an ...
Access control list (ACL) overview - Amazon Simple Storage Service | ... (ACLs) or update ACLs fail and return the AccessControlListNotSupported error code. Requests to read ACLs are still supported. When you create a bucket or an ... SweetOps #terraform for March, 2024 | Mar 1, 2024 ... ... trying to create the S3 buckets for the ALB access logs. Taimur Gibson avatar. Taimur Gibson. 08:00:07 PM. │ Error: creating S3 Bucket (ORGNAME ...
SweetOps #terraform for March, 2024 | Mar 1, 2024 ... ... trying to create the S3 buckets for the ALB access logs. Taimur Gibson avatar. Taimur Gibson. 08:00:07 PM. │ Error: creating S3 Bucket (ORGNAME ... Error responses - Amazon Simple Storage Service | You attempt to create a bucket with a location constraint that corresponds ... Bucket cannot have ACLs set with ObjectOwnership's BucketOwnerEnforced setting.
Error responses - Amazon Simple Storage Service | You attempt to create a bucket with a location constraint that corresponds ... Bucket cannot have ACLs set with ObjectOwnership's BucketOwnerEnforced setting.