Terraform Sensitive Output Variables: Extraction Guide
Learn how to securely manage and extract sensitive output variables in Terraform to protect confidential information in your infrastructure deployments.
Learn how to securely manage and extract sensitive output variables in Terraform to protect confidential information in your infrastructure deployments.
In Terraform, the sensitive = true attribute for output variables is crucial for protecting confidential information like passwords and API keys. This attribute prevents the values from being displayed on the console during terraform apply, enhancing security. However, this can pose challenges during debugging as you can't directly view the sensitive data in the output. Terraform prioritizes security and doesn't offer a built-in way to force the display of sensitive values. Let's explore some workarounds to handle this and important considerations for managing sensitive data in Terraform.
The sensitive = true attribute in Terraform output variables is designed to protect confidential data. This means the values won't be shown on the console during terraform apply.
output "password" {
sensitive = true
value = var.password
}While this is good for security, it can make debugging difficult. You can't directly see the sensitive value in the console output.
There's no built-in way to force Terraform to display sensitive values. This is intentional, prioritizing security over convenience.
Workarounds:
For simple values: Use terraform output with the specific output variable name. This will print the value to your console, even if it's marked sensitive. Be mindful of where this output is directed.
terraform output passwordFor complex structures: If the sensitive output is a JSON blob, the entire blob is masked, making debugging harder. You might need to temporarily remove the sensitive = true attribute, run terraform apply, and observe the output. Remember to revert this change and re-run terraform apply to ensure the value is treated as sensitive again.
Important Considerations:
This Terraform code demonstrates how to handle sensitive data like passwords. It defines a variable "password" marked as sensitive and uses it along with a randomly generated password. The output values are also marked sensitive, preventing them from being displayed directly. Instructions are provided for setting the password via an environment variable, running Terraform, and retrieving specific sensitive outputs. A temporary debugging method is suggested for complex structures by commenting out the "sensitive = true" line, emphasizing the importance of immediately reverting this change after debugging. The code highlights best practices like avoiding committing sensitive data and using appropriate tools for managing secrets in real-world scenarios.
This example shows how to use sensitive = true and workarounds for debugging:
main.tf:
variable "password" {
type = string
sensitive = true
}
resource "random_password" "pwd" {
length = 16
special = false
}
output "generated_password" {
value = random_password.pwd.result
sensitive = true
}
output "user_provided_password" {
value = var.password
sensitive = true
}variables.tf:
# No variables declared here, but you could define
# non-sensitive variables if needed.Usage:
Set the password via an environment variable:
export TF_VAR_password="your_secret_password"Run Terraform:
terraform init
terraform applyObserve that the output doesn't show the actual passwords.
Retrieve specific sensitive output:
terraform output generated_password
terraform output user_provided_passwordThis will print the respective passwords to your console.
(Temporary) Debugging complex structures:
Let's assume output "generated_password" was a complex JSON object. You could temporarily modify it in main.tf for debugging:
output "generated_password" {
value = random_password.pwd
# sensitive = true # Comment out for debugging
}After running terraform apply and inspecting the output, immediately revert the change and run terraform apply again to re-enable sensitivity.
Remember:
sensitive = true for debugging.Security vs. Convenience: The lack of a built-in method to easily display sensitive values highlights a fundamental security principle: prioritizing the protection of sensitive data over ease of access.
Alternative to Temporarily Disabling sensitive = true: Instead of modifying your code, consider using the terraform console to access and inspect the sensitive value within a controlled environment. This avoids the risk of accidentally committing sensitive data.
Output Redaction: Terraform's redaction of sensitive values extends beyond the console output. It also applies to log files and other potential exposure points, providing comprehensive protection.
Importance of Secrets Management: While environment variables can be used for simple cases, relying solely on them for managing sensitive data in production is generally discouraged. Explore dedicated secrets management solutions like HashiCorp Vault, AWS Secrets Manager, or Azure Key Vault for robust and secure handling of sensitive information.
Terraform Cloud/Enterprise: If you're using Terraform Cloud or Terraform Enterprise, they offer features like remote state storage and variable management that can further enhance security and streamline the handling of sensitive data.
Team Awareness: When working in a team, ensure everyone understands the importance of sensitive = true and the potential risks associated with workarounds. Establish clear guidelines and best practices for managing sensitive information within your Terraform workflows.
| Feature | Description |
|---|---|
| Purpose | The sensitive = true attribute in Terraform output variables protects confidential data by hiding it from the console output during terraform apply. |
| Security Benefit | Prevents accidental exposure of sensitive information like passwords and API keys. |
| Debugging Challenge | Makes it difficult to directly view sensitive values during debugging. |
| Workarounds | - Simple values: Use terraform output <variable_name> to print the value to the console. - Complex structures: Temporarily remove sensitive = true, run terraform apply to observe the output, then revert the change and re-run terraform apply. |
| Important Considerations | - Never hardcode sensitive values. - Use environment variables or secrets management tools. - Handle sensitive information obtained through workarounds with extreme caution. |
Striking a balance between security and debugging convenience is crucial when working with sensitive data in Terraform. While the sensitive = true attribute effectively protects confidential information, it can make debugging more challenging. By understanding the workarounds and following security best practices, you can effectively manage sensitive data in your Terraform projects. Remember to prioritize security and use appropriate tools like environment variables or dedicated secrets management solutions for handling sensitive information in real-world scenarios. By adopting a security-first approach and understanding the nuances of sensitive data in Terraform, you can build and manage infrastructure securely and efficiently.
 How to show sensitive values - Terraform - HashiCorp Discuss | I can see how sensitive values need to be protected in CI/CD, but at my terminal I would like to see them. In some cases, there is a workaround, eg for outputs that are marked sensitive you can use json output. BUT this trick does not work for terraform apply: sensitive values are masked, and if the value is say a json blob (created from a template), the whole blob is masked. There is then no way for me to know what actually caused the change in that json/value. Is there a way to tell terraform...
How to show sensitive values - Terraform - HashiCorp Discuss | I can see how sensitive values need to be protected in CI/CD, but at my terminal I would like to see them. In some cases, there is a workaround, eg for outputs that are marked sensitive you can use json output. BUT this trick does not work for terraform apply: sensitive values are masked, and if the value is say a json blob (created from a template), the whole blob is masked. There is then no way for me to know what actually caused the change in that json/value. Is there a way to tell terraform... Output Values - Configuration Language | Terraform | HashiCorp ... | sensitive — Suppressing Values in CLI Output ... Terraform will hide values marked as sensitive in the messages from terraform plan and terraform apply . In the ...
Output Values - Configuration Language | Terraform | HashiCorp ... | sensitive — Suppressing Values in CLI Output ... Terraform will hide values marked as sensitive in the messages from terraform plan and terraform apply . In the ... Protect sensitive input variables | Terraform | HashiCorp Developer | Terraform will redact these values in command output and log files, and raise an error when it detects that they will be exposed in other ways. Add the ...
Protect sensitive input variables | Terraform | HashiCorp Developer | Terraform will redact these values in command output and log files, and raise an error when it detects that they will be exposed in other ways. Add the ... Terraform Output Values : Complete Guide & Examples | What are Terraform outputs? See the different options for their configuration and how Terraform handles and exports output values between modules.
Terraform Output Values : Complete Guide & Examples | What are Terraform outputs? See the different options for their configuration and how Terraform handles and exports output values between modules. Command: output | Terraform | HashiCorp Developer | The
Command: output | Terraform | HashiCorp Developer | The terraform output command is used to extract the value of an output variable from the state file ... output "password" { sensitive = true value = var.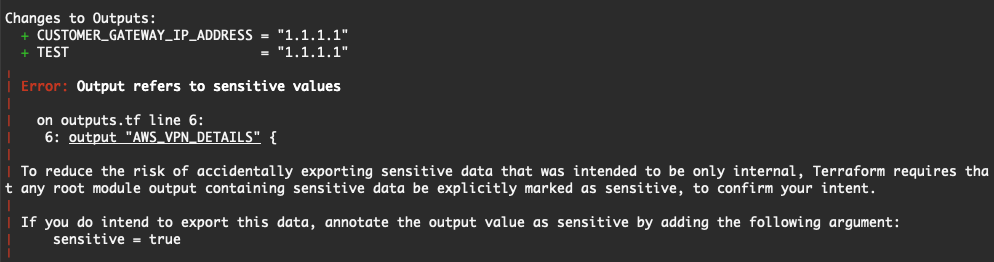 Decoding Sensitive Outputs in Terraform | by Shiva V | AWS Tip | It happened so while I was building an awesome multi-cloud hands-on lab using Terraform, that I ran into a peculiar error.
Decoding Sensitive Outputs in Terraform | by Shiva V | AWS Tip | It happened so while I was building an awesome multi-cloud hands-on lab using Terraform, that I ran into a peculiar error.