Terraform Provider Checksum Mismatch: Fix Install Error
Learn how to troubleshoot and resolve checksum mismatch errors in Terraform when the downloaded provider doesn't match the dependency lock file.
Learn how to troubleshoot and resolve checksum mismatch errors in Terraform when the downloaded provider doesn't match the dependency lock file.
When working with Terraform, encountering the error message "Failed to install provider, doesn't match checksums" can be perplexing. This issue signals a discrepancy between the Terraform provider version you want to use and the version recorded in your project's dependency lock file, .terraform.lock.hcl. This file plays a crucial role in maintaining consistent provider versions across different environments and preventing unexpected changes during Terraform operations like terraform init or terraform apply. Let's delve into the common causes of this error and explore the steps to resolve it effectively.
The error message "Failed to install provider, doesn't match checksums" in Terraform indicates a mismatch between the provider version you're trying to use and the version recorded in your dependency lock file (.terraform.lock.hcl). This file ensures consistent provider versions across different environments and prevents unexpected changes during terraform init or terraform apply.
Here's a breakdown of how to resolve this issue:
Understand the Cause: This error typically arises when someone attempts to initialize Terraform with a different provider version than the one specified in the lock file. This discrepancy can stem from various scenarios, including:
Resolution Steps:
Update the Lock File: The most common solution is to regenerate the lock file, ensuring it aligns with the desired provider versions:
terraform init -upgradeThis command fetches the latest provider versions compatible with your configuration and updates the lock file accordingly.
Verify Provider Constraints: Double-check the version constraints in your Terraform configuration files (e.g., required_providers blocks) to ensure they match your intended versions.
Inspect Changes: If the issue persists, carefully review recent changes to your Terraform configuration, particularly modifications to provider versions or the addition of new providers.
Best Practices:
.terraform.lock.hcl file in your version control system (e.g., Git) to maintain consistency across your team and environments.terraform init -upgrade to manage provider versions and update the lock file.By following these steps and adhering to best practices, you can effectively address checksum mismatches and ensure the reliability of your Terraform deployments.
This text describes a scenario where the Terraform configuration specifies AWS provider version 4.0.0, but the .terraform.lock.hcl file has version 3.0.0. This mismatch causes a "Failed to install provider, doesn't match checksums" error during terraform init. To resolve this, run terraform init -upgrade to download the correct provider version and update the lock file. Finally, verify the updated version in the lock file and commit the changes.
Let's say you have a Terraform configuration using the AWS provider. Your .terraform.lock.hcl file specifies version 3.0.0, but you've updated your configuration to use version 4.0.0 without updating the lock file.
main.tf:
terraform {
required_providers {
aws = {
source = "hashicorp/aws"
version = "~> 4.0.0" # Updated version
}
}
}
# ... rest of your configuration.terraform.lock.hcl (outdated):
# ... other providers
provider "registry.terraform.io/hashicorp/aws" {
version = "3.0.0" # Outdated version
}Running terraform init will result in the "Failed to install provider, doesn't match checksums" error.
Update the Lock File:
terraform init -upgradeThis command will:
4.0.0 as specified in your configuration..terraform.lock.hcl file to reflect the new version:.terraform.lock.hcl (updated):
# ... other providers
provider "registry.terraform.io/hashicorp/aws" {
version = "4.0.0" # Updated version
}Verify and Commit:
version in your .terraform.lock.hcl file now matches the desired version (4.0.0 in this example)..terraform.lock.hcl file to your version control system.Now, subsequent terraform init commands will use the correct provider version, ensuring consistency and preventing checksum errors.
terraform init -upgrade again..terraform/plugins directory in your project. Then run terraform init to re-download the providers.This error means the provider version you're using doesn't match the version in your .terraform.lock.hcl file, which ensures consistent provider versions across environments.
Causes:
Resolution:
terraform init -upgrade to fetch the latest compatible provider versions and update the lock file.Best Practices:
.terraform.lock.hcl in version control.terraform init -upgrade to manage provider versions and update the lock file.By understanding the role of the .terraform.lock.hcl file and following the outlined resolution steps and best practices, you can effectively troubleshoot and prevent checksum mismatches in your Terraform projects. Maintaining consistency in provider versions is vital for predictable and reliable infrastructure deployments, and addressing these errors proactively contributes to a smoother and more secure Terraform workflow.
 Provider lock hash list value changed - Terraform - HashiCorp Discuss | I have a terraform config directory and I use atlantis to run terraform commands. Today, someone submitted a PR to add some new config to the directory. The terraform init came back with: Initializing the backend... Initializing modules... Initializing provider plugins... - terraform.io/builtin/terraform is built in to Terraform - Reusing previous version of confluentinc/confluent from the dependency lock file - Reusing previous version of hashicorp/aws from the dependency lock file - Using co...
Provider lock hash list value changed - Terraform - HashiCorp Discuss | I have a terraform config directory and I use atlantis to run terraform commands. Today, someone submitted a PR to add some new config to the directory. The terraform init came back with: Initializing the backend... Initializing modules... Initializing provider plugins... - terraform.io/builtin/terraform is built in to Terraform - Reusing previous version of confluentinc/confluent from the dependency lock file - Reusing previous version of hashicorp/aws from the dependency lock file - Using co... Dependency Lock File (.terraform.lock.hcl) - Configuration Language | 0 doesn't match any of the checksums previously recorded in the dependency lock file. Error: Failed to install provider Error while installing hashicorp/azurerm ...
Dependency Lock File (.terraform.lock.hcl) - Configuration Language | 0 doesn't match any of the checksums previously recorded in the dependency lock file. Error: Failed to install provider Error while installing hashicorp/azurerm ...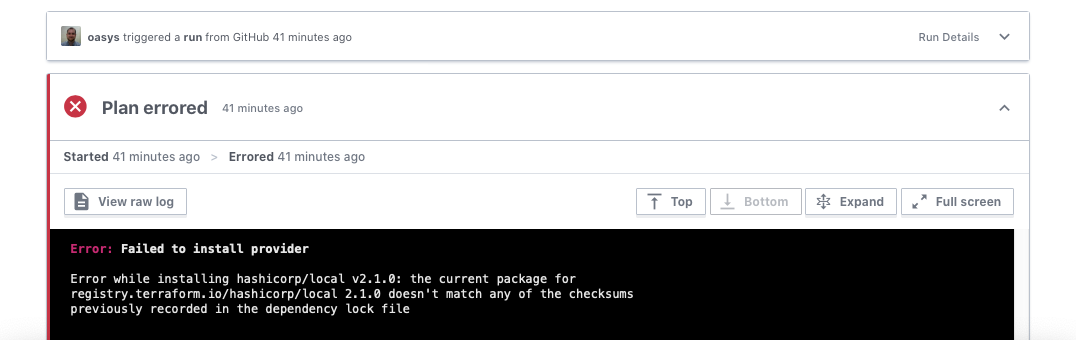 Terraform providers lock | Oasys Networking | Resolving missing hashes in the Terraform dependency lock file.
Terraform providers lock | Oasys Networking | Resolving missing hashes in the Terraform dependency lock file.