Kubernetes Secrets vs ConfigMaps: When to Use Which?
Learn when to leverage Kubernetes Secrets for sensitive data and when ConfigMaps are suitable for configuration settings in your applications.
Learn when to leverage Kubernetes Secrets for sensitive data and when ConfigMaps are suitable for configuration settings in your applications.
In Kubernetes, managing application configuration and sensitive data effectively is crucial for portability and security. ConfigMaps and Secrets provide mechanisms to store this data externally from your codebase. This separation enhances flexibility and allows for easier management of different environments. Let's explore when to use each and understand their key differences.
Both ConfigMaps and Secrets are used in Kubernetes to store data externally from your application code, promoting portability and flexibility.
Let's say you have a database connection string:
db_host=my-database
db_user=admin
db_password=MySuperSecretPassword
When to use ConfigMaps:
Example:
apiVersion: v1
kind: ConfigMap
metadata:
name: my-config
data:
db_host: my-database
db_user: adminWhen to use Secrets:
Example:
apiVersion: v1
kind: Secret
metadata:
name: my-secret
type: Opaque
data:
db_password: TXlTdXBlclNlY3JldFBhc3N3b3JkKey Differences:
Important Considerations:
This code provides an example of managing database connection details in Kubernetes using ConfigMaps and Secrets. A ConfigMap stores non-sensitive data like database host and username. A Secret securely stores the sensitive database password in base64 encoded format. A Deployment configuration demonstrates how to use these ConfigMaps and Secrets to inject environment variables into a container, allowing the application to access database connection details securely. The example also includes commands to apply these configurations using kubectl.
This example demonstrates how to use ConfigMaps and Secrets to manage database connection details in a Kubernetes deployment.
1. Create a ConfigMap for non-sensitive data:
apiVersion: v1
kind: ConfigMap
metadata:
name: db-config
data:
db_host: my-database
db_user: admin2. Create a Secret for the sensitive password:
apiVersion: v1
kind: Secret
metadata:
name: db-secret
type: Opaque
data:
db_password: TXlTdXBlclNlY3JldFBhc3N3b3Jk # Base64 encoded "MySuperSecretPassword"3. Create a Deployment that uses both ConfigMap and Secret:
apiVersion: apps/v1
kind: Deployment
metadata:
name: my-app
spec:
replicas: 1
selector:
matchLabels:
app: my-app
template:
metadata:
labels:
app: my-app
spec:
containers:
- name: my-app-container
image: <your-app-image>
env:
- name: DB_HOST
valueFrom:
configMapKeyRef:
name: db-config
key: db_host
- name: DB_USER
valueFrom:
configMapKeyRef:
name: db-config
key: db_user
- name: DB_PASSWORD
valueFrom:
secretKeyRef:
name: db-secret
key: db_passwordExplanation:
db_host and db_user in a ConfigMap named db-config.db_password is stored base64 encoded in a Secret named db-secret.DB_HOST, DB_USER, DB_PASSWORD) within the container.configMapKeyRef to fetch values from the db-config ConfigMap.secretKeyRef to fetch the password from the db-secret Secret.Applying the configuration:
You can apply these configurations using kubectl:
kubectl apply -f configmap.yaml
kubectl apply -f secret.yaml
kubectl apply -f deployment.yamlThis setup ensures that sensitive data is handled securely while keeping your application code independent of specific configuration values. Remember that while Secrets offer a basic level of obfuscation, consider using a dedicated secrets management solution for enhanced security in production environments.
Security:
Best Practices:
Alternatives to Consider:
Remember: Security is an ongoing process. Regularly review and update your security practices and tools to mitigate risks.
| Feature | ConfigMap | Secret |
|---|---|---|
| Purpose | Store non-sensitive configuration data | Store sensitive data like passwords and API keys |
| Data Storage | Plain text | Base64 encoded |
| Security | No obfuscation | Basic obfuscation, not suitable for highly sensitive data |
| Example Use Case | Database hostname, application settings | Database password, API tokens |
| Accessibility | Mountable as volumes, exposed as environment variables | Same as ConfigMaps |
Key Takeaways:
In conclusion, ConfigMaps and Secrets are essential tools in Kubernetes for managing application configuration and sensitive data, respectively. While Secrets offer a basic level of obfuscation through base64 encoding, it's crucial to remember that neither mechanism provides ironclad security. For highly sensitive information, adopting a dedicated secrets management solution is non-negotiable. By understanding the strengths, limitations, and best practices associated with ConfigMaps and Secrets, developers can leverage these Kubernetes objects to build secure, portable, and easily manageable applications.
 In-Depth Guide to Kubernetes ConfigMap & Secret Management ... | Nov 15, 2023 ... ConfigMaps stores data as key-value pairs, whereas Secrets stores data as base64-encoded data, thereby ensuring an additional layer of security.
In-Depth Guide to Kubernetes ConfigMap & Secret Management ... | Nov 15, 2023 ... ConfigMaps stores data as key-value pairs, whereas Secrets stores data as base64-encoded data, thereby ensuring an additional layer of security. Difference between Kubernetes ConfigMaps and Secrets | CloudTruth | Learn differences between ConfigMaps and Secrets. Both are stored the same way, but ConfigMaps are plain text and secrets are only for apps.
Difference between Kubernetes ConfigMaps and Secrets | CloudTruth | Learn differences between ConfigMaps and Secrets. Both are stored the same way, but ConfigMaps are plain text and secrets are only for apps.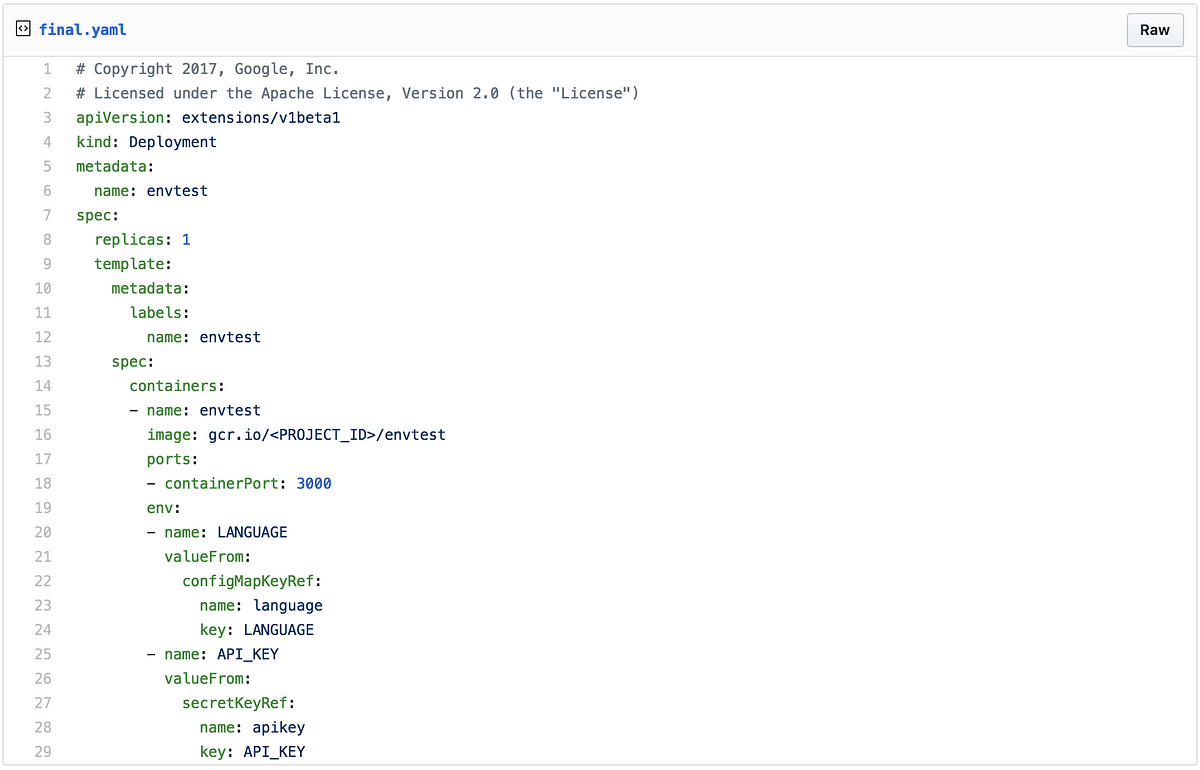 Kubernetes ConfigMaps and Secrets | by Sandeep Dinesh | Google ... | Everyone needs to configure applications. You often need to reference “special” bits of data, such as API keys, tokens, and other secrets…
Kubernetes ConfigMaps and Secrets | by Sandeep Dinesh | Google ... | Everyone needs to configure applications. You often need to reference “special” bits of data, such as API keys, tokens, and other secrets… Secrets | Kubernetes | A Secret is an object that contains a small amount of sensitive data such as a password, a token, or a key. Such information might otherwise be put in a Pod specification or in a container image. Using a Secret means that you don't need to include confidential data in your application code.
Because Secrets can be created independently of the Pods that use them, there is less risk of the Secret (and its data) being exposed during the workflow of creating, viewing, and editing Pods.
Secrets | Kubernetes | A Secret is an object that contains a small amount of sensitive data such as a password, a token, or a key. Such information might otherwise be put in a Pod specification or in a container image. Using a Secret means that you don't need to include confidential data in your application code.
Because Secrets can be created independently of the Pods that use them, there is less risk of the Secret (and its data) being exposed during the workflow of creating, viewing, and editing Pods. Kubernetes Configmaps and Secrets | Create and Update | Kubernetes ConfigMaps and Secrets are Kubernetes resources that you can use to separate configuration from pod specs.
Kubernetes Configmaps and Secrets | Create and Update | Kubernetes ConfigMaps and Secrets are Kubernetes resources that you can use to separate configuration from pod specs. ConfigMaps | Kubernetes | A ConfigMap is an API object used to store non-confidential data in key-value pairs. Pods can consume ConfigMaps as environment variables, command-line arguments, or as configuration files in a volume.
A ConfigMap allows you to decouple environment-specific configuration from your container images, so that your applications are easily portable.
Caution:ConfigMap does not provide secrecy or encryption. If the data you want to store are confidential, use a Secret rather than a ConfigMap, or use additional (third party) tools to keep your data private.
ConfigMaps | Kubernetes | A ConfigMap is an API object used to store non-confidential data in key-value pairs. Pods can consume ConfigMaps as environment variables, command-line arguments, or as configuration files in a volume.
A ConfigMap allows you to decouple environment-specific configuration from your container images, so that your applications are easily portable.
Caution:ConfigMap does not provide secrecy or encryption. If the data you want to store are confidential, use a Secret rather than a ConfigMap, or use additional (third party) tools to keep your data private. Kubernetes 101: Secret and ConfigMap | by 8grams | Medium | Introduction to Kubernetes Secrets
Kubernetes 101: Secret and ConfigMap | by 8grams | Medium | Introduction to Kubernetes Secrets Kubernetes ConfigMaps and Secrets: When to Use Them? | Learn how Kubernetes ConfigMaps and Secrets work, see if they interact with CAST AI, and what that means for your config security.
Kubernetes ConfigMaps and Secrets: When to Use Them? | Learn how Kubernetes ConfigMaps and Secrets work, see if they interact with CAST AI, and what that means for your config security.