GCP IAM: Understanding Authoritative and Authoritative Members
Learn the difference between "authoritative" and "authoritative" IAM member types in Google Cloud Platform and how they impact permissions and resource access.
Learn the difference between "authoritative" and "authoritative" IAM member types in Google Cloud Platform and how they impact permissions and resource access.
In Google Cloud Platform (GCP), Identity and Access Management (IAM) is essential for controlling access to resources. When using infrastructure-as-code tools like Terraform or Pulumi, understanding "authoritative" and "non-authoritative" IAM management is crucial.
In Google Cloud Platform (GCP), managing permissions is crucial for controlling access to your resources. You can manage these permissions using Identity and Access Management (IAM). When working with infrastructure-as-code tools like Terraform or Pulumi, you'll encounter the concepts of "authoritative" and "non-authoritative" IAM management. Let's break down these concepts:
Authoritative IAM Management
Think of "authoritative" as setting the absolute rules for who can access your GCP resources. When you manage IAM in an authoritative way, you're telling GCP: "These are the ONLY permissions that should exist. Anything else should be removed."
Here's how it works:
Non-Authoritative IAM Management
"Non-authoritative" is a more permissive approach. It's like saying, "I want to add these permissions, but I don't necessarily want to touch any existing ones."
Here's the breakdown:
When to Use Each Approach
Example Scenario
Imagine you have a GCS bucket.
Authoritative: You use Terraform to define that only your "data-science-team" group should have read access. Terraform will remove any other existing permissions on the bucket, ensuring only the data science team has access.
Non-Authoritative: You use Terraform to grant the "data-analyst" group write access to the bucket. Terraform adds this permission without affecting any other existing permissions on the bucket.
Important Considerations
The code demonstrates the difference between authoritative and non-authoritative IAM management for a Google Cloud Storage bucket using Terraform. The first example shows authoritative management where only the explicitly defined "data-science-team" group is granted access to the bucket, while any other existing permissions are removed. The second example illustrates non-authoritative management where the "data-analyst" group is granted access without affecting any other existing permissions on the bucket. The choice between these approaches depends on the desired level of control and flexibility required for managing access to the bucket.
Let's illustrate the concepts with Terraform code examples for managing permissions on a Google Cloud Storage (GCS) bucket.
Scenario: We have a GCS bucket named "my-bucket" and want to manage access for two groups: "data-science-team" and "data-analyst".
1. Authoritative IAM Management
resource "google_storage_bucket" "example" {
name = "my-bucket"
location = "US"
force_destroy = false
}
resource "google_storage_bucket_iam_member" "data_science_team" {
bucket = google_storage_bucket.example.name
role = "roles/storage.objectViewer"
member = "group:data-science-team@example.com"
}Explanation:
google_storage_bucket_iam_member to grant the "data-science-team" group the "Storage Object Viewer" role.2. Non-Authoritative IAM Management
resource "google_storage_bucket" "example" {
name = "my-bucket"
location = "US"
force_destroy = false
}
resource "google_storage_bucket_iam_binding" "data_analyst" {
bucket = google_storage_bucket.example.name
role = "roles/storage.objectCreator"
members = [
"group:data-analyst@example.com",
]
}Explanation:
google_storage_bucket_iam_binding to grant the "data-analyst" group the "Storage Object Creator" role.Key Takeaways:
Remember to consult the official documentation for Terraform and Google Cloud IAM for the most up-to-date information and best practices.
Remember: IAM is a fundamental aspect of security in GCP. By understanding the concepts of authoritative and non-authoritative management and following best practices, you can effectively control access to your resources and maintain a secure cloud environment.
| Feature | Authoritative | Non-Authoritative |
|---|---|---|
| Definition | Sets absolute permissions, removing any not explicitly defined. | Adds specified permissions without affecting existing ones. |
| Control Level | Strict | Flexible |
| Process | 1. Define desired state. 2. Tool enforces definition, deleting extraneous permissions. 3. Complete control achieved. |
1. Define permissions to add. 2. Tool adds permissions without removing existing ones. 3. Flexibility maintained, potential for permission sprawl. |
| Use Cases | - Security-sensitive resources. - Enforcing strict access control. |
- Collaboration on resources with shared permission management. - Adding permissions without disrupting existing access. |
| Example | Granting read access to a GCS bucket only to the "data-science-team" group, removing all other permissions. | Granting write access to a GCS bucket to the "data-analyst" group, while preserving existing permissions. |
| Advantages | - Enhanced security. - Prevents permission creep. |
- Flexibility in collaborative environments. - Easier to add permissions incrementally. |
| Disadvantages | - Less flexible. - Requires careful planning to avoid accidental access removal. |
- Potential for permission sprawl. - Reduced security if not managed diligently. |
Important Notes:
Understanding the difference between authoritative and non-authoritative IAM management in GCP is crucial for maintaining a secure and well-managed cloud environment. Authoritative management enforces strict control over permissions, ensuring only explicitly defined access is granted, while non-authoritative management offers flexibility by adding permissions without modifying existing ones. When to use each approach depends on your specific security requirements, the sensitivity of your resources, and your team's collaborative needs. Regularly review and update your IAM policies, leverage GCP tools for simplified management, and prioritize the principle of least privilege to maintain a secure and well-organized GCP environment.
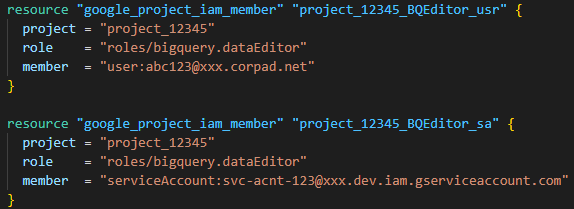 Authoritative Vs non-Authoritative Terraform resources for GCP IAM ... | Once the services/resources (like GCS bucket, BigQuery dataset) are deployed to GCP, permissions are needed to access those…
Authoritative Vs non-Authoritative Terraform resources for GCP IAM ... | Once the services/resources (like GCS bucket, BigQuery dataset) are deployed to GCP, permissions are needed to access those… gcp.serviceaccount.IAMBinding | Pulumi Registry | Documentation for the gcp.serviceaccount.IAMBinding resource with examples, input properties, output properties, lookup functions, and supporting types.
gcp.serviceaccount.IAMBinding | Pulumi Registry | Documentation for the gcp.serviceaccount.IAMBinding resource with examples, input properties, output properties, lookup functions, and supporting types. gcp.artifactregistry.RepositoryIamBinding | Pulumi Registry | Documentation for the gcp.artifactregistry.RepositoryIamBinding resource with examples, input properties, output properties, lookup functions, and supporting types.
gcp.artifactregistry.RepositoryIamBinding | Pulumi Registry | Documentation for the gcp.artifactregistry.RepositoryIamBinding resource with examples, input properties, output properties, lookup functions, and supporting types. gcp.projects.IAMBinding | Pulumi Registry | Documentation for the gcp.projects.IAMBinding resource with examples, input properties, output properties, lookup functions, and supporting types.
gcp.projects.IAMBinding | Pulumi Registry | Documentation for the gcp.projects.IAMBinding resource with examples, input properties, output properties, lookup functions, and supporting types. What is the need for ACL s when GCP already has Cloud IAM ... | What is the need for ACL's when GCP already has Cloud IAM permissions for the controlling the access to resources?
What is the need for ACL s when GCP already has Cloud IAM ... | What is the need for ACL's when GCP already has Cloud IAM permissions for the controlling the access to resources? Terraform Module for GCP KMS Keyrings & Keys : r/Terraform | Posted by u/[Deleted Account] - 10 votes and 2 comments
Terraform Module for GCP KMS Keyrings & Keys : r/Terraform | Posted by u/[Deleted Account] - 10 votes and 2 comments