eksctl create iamserviceaccount Explained: EKS Deep Dive
Learn how "eksctl create iamserviceaccount" simplifies IAM role creation and binding for your EKS deployments within your Terraform configurations.
Learn how "eksctl create iamserviceaccount" simplifies IAM role creation and binding for your EKS deployments within your Terraform configurations.
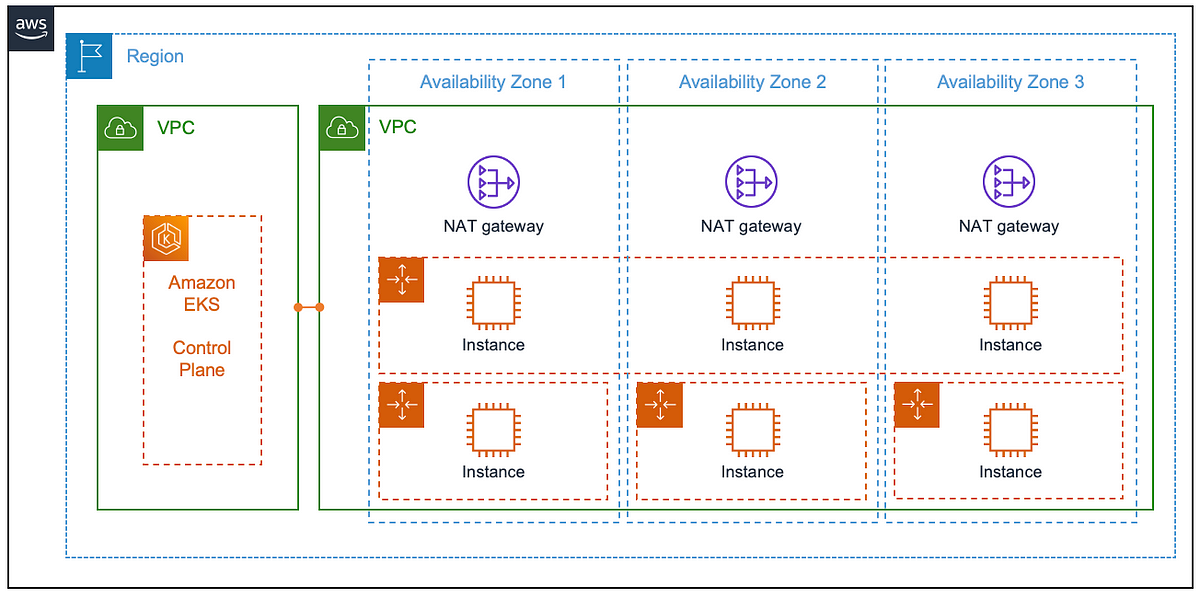
terraform:Managing AWS permissions for your Kubernetes pods running on Amazon EKS is crucial for secure and controlled access to AWS services. The eksctl create iamserviceaccount command simplifies this process significantly. Here's a step-by-step explanation of how it works:
The command eksctl create iamserviceaccount streamlines the process of granting AWS permissions to your Kubernetes pods running on an Amazon EKS cluster. Here's a breakdown of what happens behind the scenes:
IAM Role Creation: It creates an IAM role in your AWS account. This role is designed to be assumable by the Kubernetes service account you're about to create.
Trust Relationship Establishment: It configures a trust relationship between the IAM role and the EKS service account. This relationship allows the Kubernetes service account to assume the IAM role when needed.
Service Account Creation: It creates a service account within your specified Kubernetes namespace. This service account acts as the identity for your pods.
Annotation for IAM Role Association: It annotates the service account with the Amazon EKS-specific annotation eks.amazonaws.com/role-arn. This annotation links the service account to the IAM role created earlier.
AWS SDK Utilization (Within Pods): When a pod associated with this service account runs and needs to interact with AWS services, the AWS SDK (or similar tools) will automatically detect the service account's linked IAM role.
Temporary Credentials Retrieval: The AWS SDK leverages the IAM Roles for Service Accounts (IRSA) mechanism to obtain temporary AWS credentials from the linked IAM role.
Secure AWS API Calls: Your pod can now use these temporary credentials to make authenticated calls to AWS APIs, accessing only the resources permitted by the IAM role's policy.
Key Points:
eksctl automates these steps, simplifying the configuration process compared to manual setup.Alternatives:
While eksctl offers a convenient way to manage IAM roles for service accounts, alternative tools like terraform can also achieve this. The fundamental steps and concepts remain similar regardless of the tool used.
This code provides examples of how to grant AWS permissions to Kubernetes pods using either the eksctl command-line tool or HashiCorp terraform. Both methods involve creating an IAM role with an attached policy that grants access to specific AWS resources, such as S3 buckets. The eksctl method simplifies the process by creating both the service account and IAM role, while the terraform method offers more granular control over the resources. Once configured, pods associated with the service account can leverage the attached IAM role to interact with AWS services without requiring explicit credentials.
# Create an IAM role for your pods
eksctl create iamserviceaccount \
--cluster=<your-cluster-name> \
--namespace=<your-namespace> \
--name=<your-service-account-name> \
--attach-policy-arn=arn:aws:iam::<your-account-id>:policy/<your-iam-policy-name> \
--override-existing-serviceaccounts Explanation:
--cluster: Specifies your EKS cluster name.--namespace: Specifies the Kubernetes namespace where the service account will be created.--name: Defines the name for your service account.--attach-policy-arn: Attaches an existing IAM policy to the created IAM role. Replace placeholders with your actual values.--override-existing-serviceaccounts: Updates an existing service account if one with the same name already exists.Example IAM Policy (replace placeholders):
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"s3:GetObject",
"s3:PutObject"
],
"Resource": "arn:aws:s3:::<your-bucket-name>/*"
}
]
}Accessing AWS Services from a Pod:
import boto3
# No need to provide explicit credentials, the SDK will use the pod's role
s3_client = boto3.client('s3')
# Interact with S3
s3_client.download_file('<your-bucket-name>', '<object-key>', '/tmp/downloaded-file')resource "aws_iam_role" "eks_pod_role" {
name = "eks-pod-role"
assume_role_policy = <<POLICY
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"Federated": "arn:aws:iam::<your-account-id>:oidc-provider/server.amazonaws.com/us-west-2/<your-cluster-name>"
},
"Action": "sts:AssumeRoleWithWebIdentity",
"Condition": {
"StringEquals": {
"server.amazonaws.com/us-west-2/<your-cluster-name>:sub": "system:serviceaccount:<your-namespace>:<your-service-account-name>"
}
}
}
]
}
POLICY
}
resource "aws_iam_role_policy_attachment" "eks_pod_role_policy_attachment" {
role = aws_iam_role.eks_pod_role.name
policy_arn = "arn:aws:iam::<your-account-id>:policy/<your-iam-policy-name>"
}
resource "kubernetes_service_account" "example" {
metadata {
name = "your-service-account-name"
namespace = "your-namespace"
annotations = {
"eks.amazonaws.com/role-arn" = aws_iam_role.eks_pod_role.arn
}
}
}Explanation:
aws_iam_role: Defines the IAM role with a trust relationship allowing the EKS service account to assume it.aws_iam_role_policy_attachment: Attaches the desired IAM policy to the role.kubernetes_service_account: Creates the service account and annotates it with the IAM role ARN.Remember to replace all placeholders with your actual values. These examples demonstrate how to grant AWS permissions to your Kubernetes pods using eksctl and terraform. Choose the approach that best suits your workflow and infrastructure management practices.
Security Best Practices:
AmazonS3FullAccess.Troubleshooting:
eks.amazonaws.com/role-arn annotation.Advanced Concepts:
Alternatives to eksctl and terraform:
Remember: These notes provide a starting point. Always refer to the official AWS and Kubernetes documentation for the most up-to-date information and best practices.
| Feature | Description |
|---|---|
| IAM Role Creation | Creates an IAM role that can be assumed by the Kubernetes service account. |
| Trust Relationship | Establishes a trust relationship between the IAM role and the Kubernetes service account, allowing the latter to assume the former. |
| Service Account Creation | Creates a service account in your Kubernetes namespace to act as the identity for your pods. |
| IAM Role Association | Annotates the service account with the IAM role ARN using eks.amazonaws.com/role-arn. |
| AWS SDK Integration | Enables the AWS SDK within pods to automatically detect and utilize the linked IAM role. |
| Temporary Credentials | Leverages IAM Roles for Service Accounts (IRSA) to obtain temporary AWS credentials from the linked role. |
| Secure AWS API Access | Allows pods to make authenticated calls to AWS APIs using the temporary credentials, restricted by the IAM role's policy. |
Benefits:
eksctl automates the entire process.Alternatives:
terraform can achieve similar results.Key Takeaway:
eksctl create iamserviceaccount simplifies granting AWS permissions to Kubernetes pods by automating the creation and association of IAM roles, enhancing security and ease of management.
In conclusion, managing AWS permissions for your Kubernetes pods on Amazon EKS is streamlined using the eksctl create iamserviceaccount command. This command automates the creation of IAM roles and service accounts, simplifying the process of granting pods secure access to AWS services. By understanding the underlying mechanisms of IAM roles, trust relationships, service account annotations, and the AWS SDK's role assumption capabilities, you can effectively leverage this tool to enhance the security and efficiency of your Kubernetes deployments on AWS. Remember to follow security best practices, such as adhering to the principle of least privilege and regularly reviewing IAM policies. Whether you choose eksctl, terraform, or other tools, the fundamental principles of secure AWS access for Kubernetes pods remain crucial for building robust and well-protected applications on EKS.
 On Amazon EKS and cluster add-ons | by Dirk Michel | Medium | Why you should consider running cluster add-ons on AWS Fargate serverless compute.
On Amazon EKS and cluster add-ons | by Dirk Michel | Medium | Why you should consider running cluster add-ons on AWS Fargate serverless compute. Problem with Dgraph helm chart serviceAccount creation - Dgraph ... | What I want to do I want a K8s service account to be created by proper setting in Dgraph’s helm chart values.yaml file. What I did I used helm chart to install Dgraph in EKS cluster. The serviceAccount config in values.yaml Dgraph Helm Chart Values doesn’t create the K8s service account when it’s been installed though the attribute create is set as true. Both version, v21.12.0 and v23.0.1 failed. Here is my settings. serviceAccount: create: true annotations: eks.amazonaws.com/role-a...
Problem with Dgraph helm chart serviceAccount creation - Dgraph ... | What I want to do I want a K8s service account to be created by proper setting in Dgraph’s helm chart values.yaml file. What I did I used helm chart to install Dgraph in EKS cluster. The serviceAccount config in values.yaml Dgraph Helm Chart Values doesn’t create the K8s service account when it’s been installed though the attribute create is set as true. Both version, v21.12.0 and v23.0.1 failed. Here is my settings. serviceAccount: create: true annotations: eks.amazonaws.com/role-a... Amazon Web Services Connection — apache-airflow-providers ... | This command will use an existing EKS Cluster ID and create an IAM role, service account and namespace. eksctl create iamserviceaccount --cluster="< ...
Amazon Web Services Connection — apache-airflow-providers ... | This command will use an existing EKS Cluster ID and create an IAM role, service account and namespace. eksctl create iamserviceaccount --cluster="< ... Introducing fine-grained IAM roles for service accounts | AWS Open ... | Here at AWS we focus first and foremost on customer needs. In the context of access control in Amazon EKS, you asked in issue #23 of our public container roadmap for fine-grained IAM roles in EKS. To address this need, the community came up with a number of open source solutions, such as kube2iam, kiam, […]
Introducing fine-grained IAM roles for service accounts | AWS Open ... | Here at AWS we focus first and foremost on customer needs. In the context of access control in Amazon EKS, you asked in issue #23 of our public container roadmap for fine-grained IAM roles in EKS. To address this need, the community came up with a number of open source solutions, such as kube2iam, kiam, […] Deployment of 2048 Game via EKS Cluster Using Ingress | by ... | We will configure and deploy our sample application i.e 2048 Game on AWS EKS Cluster using Helm Chart
Deployment of 2048 Game via EKS Cluster Using Ingress | by ... | We will configure and deploy our sample application i.e 2048 Game on AWS EKS Cluster using Helm Chart EKS Cluster Autoscaler: 6 Best Practices For Effective Autoscaling ... | Explore the EKS Cluster Autoscaler to see how it works and get best practices to always adjust capacity to demand (and save dollars!).
EKS Cluster Autoscaler: 6 Best Practices For Effective Autoscaling ... | Explore the EKS Cluster Autoscaler to see how it works and get best practices to always adjust capacity to demand (and save dollars!). k8s | IvanBayan | Dec 5, 2022 ... I have an EKS configured with terraform module terraform-aws-eks and IRSA configured like this: ... eksctl create iamserviceaccount \ --cluster my ...
k8s | IvanBayan | Dec 5, 2022 ... I have an EKS configured with terraform module terraform-aws-eks and IRSA configured like this: ... eksctl create iamserviceaccount \ --cluster my ...