Create Azure AD App Registrations and Roles with Bicep
Learn how to automate Microsoft Entra app registration and role creation using Bicep or ARM templates for streamlined identity and access management in Azure.
Learn how to automate Microsoft Entra app registration and role creation using Bicep or ARM templates for streamlined identity and access management in Azure.
Managing Azure Active Directory (Azure AD) app registrations is a crucial aspect of deploying resources securely on Azure. While Bicep and Azure Resource Manager (ARM) excel at infrastructure provisioning, they currently lack direct support for creating Azure AD app registrations. This limitation presents challenges when you need to automate the creation of app registrations as part of your infrastructure deployments. This article explores workarounds and alternative approaches to address this limitation, enabling you to manage app registrations effectively in your Bicep deployments.
Bicep/ARM doesn't directly support creating Azure AD app registrations. This limitation means you can't directly provision app registrations within your Bicep deployments.
Workaround using Deployment Scripts:
resource deploymentScript 'Microsoft.Resources/deploymentScripts@2020-10-01' = {
name: 'createAppRegistration'
location: resourceGroup().location
properties: {
azPowerShellVersion: '7.2'
arguments: ''
primaryScriptUri: 'https://raw.githubusercontent.com/your-repo/your-script.ps1'
}
}Alternative approach using Terraform:
resource "azure_ad_application" "example" {
display_name = "example"
}Considerations:
This code defines a Bicep template and a PowerShell script to automate the creation of Azure AD app registrations. The Bicep template sets up a deployment script resource that uses a managed identity to execute the PowerShell script. The script then connects to Azure AD and creates an app registration with the specified name, outputting its details. This setup allows for streamlined and secure app registration creation within Azure deployments.
This example demonstrates how to create an Azure AD app registration using a Bicep deployment script.
Bicep Template (main.bicep):
param appRegistrationName string
resource deploymentScript 'Microsoft.Resources/deploymentScripts@2020-10-01' = {
name: 'createAppRegistration'
location: resourceGroup().location
identity: {
type: 'UserAssigned'
userAssignedIdentities: {
'${resourceId('Microsoft.ManagedIdentity/userAssignedIdentities', 'createAppRegistrationIdentity')}' : {}
}
}
properties: {
azPowerShellVersion: '7.2'
arguments: '-appName "${appRegistrationName}"'
primaryScriptUri: 'https://raw.githubusercontent.com/your-repo/create-app-registration.ps1'
}
}
resource appRegistrationIdentity 'Microsoft.ManagedIdentity/userAssignedIdentities@2018-11-30' = {
name: 'createAppRegistrationIdentity'
location: resourceGroup().location
}
// Grant the managed identity permissions to create app registrations in Azure AD
resource roleAssignment 'Microsoft.Authorization/roleAssignments@2020-10-01' = {
name: guid(appRegistrationIdentity.id, 'Application.ReadWrite.All')
scope: subscription()
properties: {
roleDefinitionId: subscriptionResourceId('Microsoft.Authorization/roleDefinitions', '1bfefb4e-c1a0-422e-a5c1-a994f25e1d3f') // Application.ReadWrite.All
principalId: appRegistrationIdentity.properties.principalId
}
}PowerShell Script (create-app-registration.ps1):
param(
[string]$appName
)
# Connect to Azure AD using the system-assigned managed identity of the deployment script
Connect-AzAccount -Identity
# Create the Azure AD app registration
$appRegistration = New-AzADApplication -DisplayName $appName
# Output the app registration details
Write-Output "App Registration Created:"
Write-Output " App ID: $($appRegistration.AppId)"
Write-Output " Display Name: $($appRegistration.DisplayName)"Explanation:
Bicep Template:
PowerShell Script:
Deployment:
main.bicep and the PowerShell script as create-app-registration.ps1.Note:
https://raw.githubusercontent.com/your-repo/create-app-registration.ps1 with the actual URL of your PowerShell script.Here are some additional notes expanding on the provided information:
Bicep/ARM Limitations:
Deployment Script Considerations:
Terraform Advantages:
Other Options:
Best Practices:
This document discusses methods for creating Azure AD app registrations using Infrastructure as Code (IaC), focusing on the limitations of Bicep/ARM and potential workarounds.
Key Takeaways:
Recommendation:
While deployment scripts offer a workaround for Bicep/ARM, using Terraform for Azure AD app registration management is recommended due to its native support, simplifying the process and potentially enhancing security.
In conclusion, while Bicep/ARM are powerful tools for Azure infrastructure deployment, they currently lack native support for Azure AD app registration. This limitation necessitates workarounds like using deployment scripts with Azure CLI or PowerShell to interact with Azure AD Graph API or Microsoft Graph. However, this approach introduces security considerations as it requires granting the script appropriate permissions. As an alternative, Terraform offers native resources for managing Azure AD app registrations, simplifying the process and potentially enhancing security. Choosing between deployment scripts and Terraform depends on factors like existing tooling, security requirements, and desired complexity level. Ultimately, automating app registration management is crucial for consistency and reducing manual errors, and choosing the right tool can significantly streamline this process.
 Support for creating AAD App registration using Bicep/ARM ... | Greetings,
Support for creating AAD App registration using Bicep/ARM ... | Greetings, App Service - Automatically Create App Registration using Bicep | HI All,
We are deploying app service on Azure using Bicep scripts. We are able to create the app service and set the required configuration using bicep.
Now, we are trying to set the Azure AD authentication and create the app registration for app…
App Service - Automatically Create App Registration using Bicep | HI All,
We are deploying app service on Azure using Bicep scripts. We are able to create the app service and set the required configuration using bicep.
Now, we are trying to set the Azure AD authentication and create the app registration for app…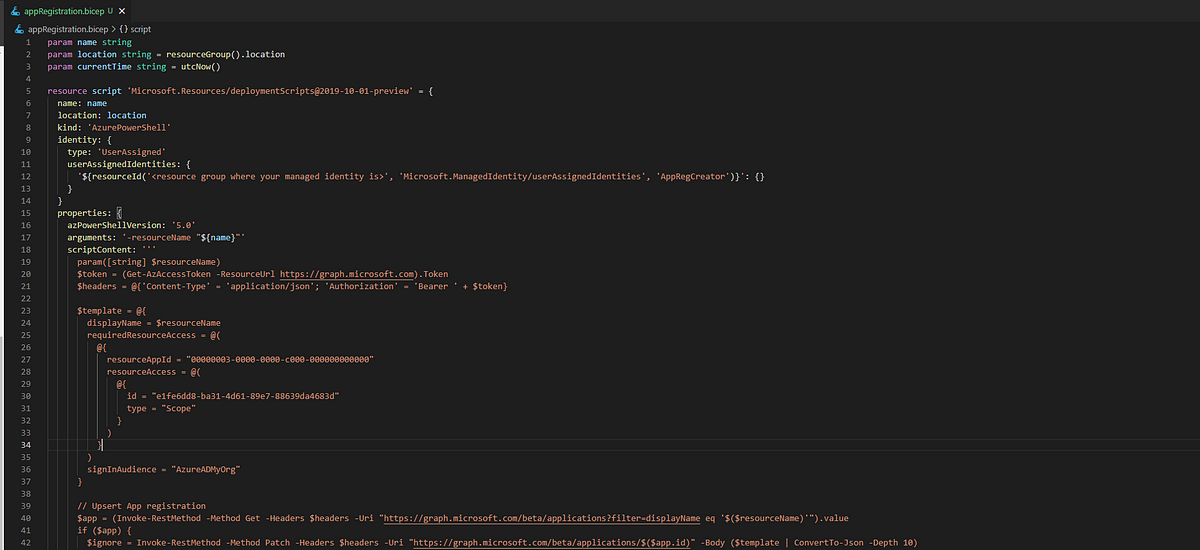 Creating App Registration with ARM templates/Bicep | by Jon ... | At the time of writing there is no Azure Resource Manager (ARM) template that can create an app registration for your applications. This…
Creating App Registration with ARM templates/Bicep | by Jon ... | At the time of writing there is no Azure Resource Manager (ARM) template that can create an app registration for your applications. This… Common errors deploying Azure Bicep and ARM templates - Blimped | Recently, I deployed some Azure resources using ARM and Bicep templates for a few customers. This is a write up of some errors I ran into.
Common errors deploying Azure Bicep and ARM templates - Blimped | Recently, I deployed some Azure resources using ARM and Bicep templates for a few customers. This is a write up of some errors I ran into. Deploy secret-less Conditional Access policies with Microsoft Entra ... |
Workload Identity Federation allows Microsoft Entra ID Conditional Access policy automation with Azure DevOps
Deploy secret-less Conditional Access policies with Microsoft Entra ... |
Workload Identity Federation allows Microsoft Entra ID Conditional Access policy automation with Azure DevOps